Business WANs
Wide Area Networks (WANs) are key in providing businesses with superior connectivity compared to the average internet user.
By utilising a WAN, employees can experience higher-quality voice communication, faster data transfers, and more responsive software access regardless of location or connection.
This article explains how business WANs work, explores the different technologies it relies on, and offers practical guidance on implementing a WAN.
Contents:
- What is a business WAN?
- How do business WANs work?
- Business WAN technologies
- Business WAN architecture
- WAN optimisation
- Reducing business WAN costs
- Advanced security strategies for WANs
What is a business WAN?
A business Wide Area Network (WAN) is a virtual network dedicated to your business’s traffic. It is formed over long distances using public internet infrastructure, connecting your business sites, cloud applications, and remote devices into a unified network.
Within this WAN, your file transfers, voice and video streams, or interactions with platforms like Google Docs will be more efficient and secure than through the public domain, resulting in a better user experience.
This superior performance is achieved by overlaying networking technologies over the internet ‘plumbing’ everyone else uses. For example, improved routing with SD-WAN and added privacy through VPNs.
Typically, the core of business WANs relies on high-performance, fully dedicated fibre connections to support business critical traffic.
However, remote workers can use standard broadband like SoGEA or 4G/5G connections to access WAN resources such as VoIP.
Who can join a business WAN?
Any authorised local network, device, or data centre can connect to your business WAN from anywhere in the world, provided the right authentication is in place. Typical examples include:
- A remote worker securely accessing your WAN via VPN over regular guest WiFi at a local café.
- A permanent connection linking your data centre hosting cloud solutions (e.g., SD-WAN or cybersecurity software) to the WAN.
- A sales agent logging in details of their site visits onto your ERP over mobile business broadband from the train.
- Field engineers in remote areas accessing your WAN over satellite internet services like Starlink, ensuring connectivity even in hard-to-reach locations.
Benefits of a business WAN
By implementing a wide area network connecting all your business assets, your organisation benefits from:
- Secure and high-speed access to shared resources such as storage systems and cloud applications.
- Voice and video communication with minimal latency, even during high-demand periods.
- Seamless collaboration on live projects with minimal latency or interruptions.
- Rapid and secure file sharing across all locations.
💡 Did you know? According to recent surveys, over 90% of enterprises consider reliable WAN connectivity critical for maintaining productivity in hybrid work environments.
How do business WANs work?
Wide Area Networks (WANs) are virtual networks that overlay advanced technologies on top of the public internet (i.e., the global web of cables, antennas, servers, etc, that connects the world).
Each of these technologies enhances how data packets are transmitted through the internet, ensuring they move more efficiently and securely. They are not mutually exclusive but work together to achieve the desired performance and security.
For instance, SD-WAN optimises data routing like a navigation app, guiding packets along the fastest and most reliable paths. Meanwhile, VPNs add a layer of encryption, effectively cloaking data to protect it from unauthorised access.
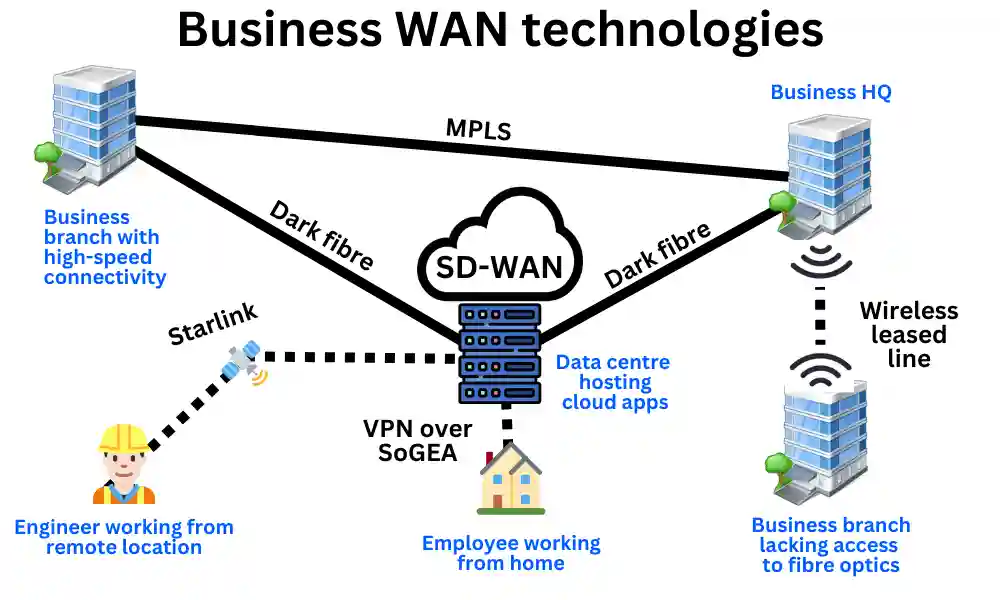
Business WAN technologies
The technologies that give rise to WANs are as follows:
SD-WAN
“The Google Maps for business data”
SD-WAN solutions (Software-Defined WAN) work like Google Maps. It monitors all available routes in your WAN, including public broadband, LTE, satellite, and private connections like leased lines, and dynamically selects the best one in real-time. This ensures critical applications like video calls always use the route with the least congestion and latency, ensuring consistent performance.
Find our more in our page on SD-WAN explained.
VPNs
“Incognito mode for business data”
A VPN (Virtual Private Network) creates a secure, encrypted “tunnel” through the public Internet. It hides data from prying eyes and protects sensitive information like your IP address. VPNs are essential for the security and privacy of remote workers, giving them access to security resources like business firewalls and confidentiality when sharing sensitive data.
Leased lines
“Exclusive roads for your business data”
Leased line broadband provides dedicated, uncontested bandwidth for your business sites. Fixed lines use fibre optic cables for high speeds, while wireless leased lines rely on radio signals for added flexibility. Both give better routes for your SD-WAN software (navigation tool) to choose from when routing your business’s traffic.
MPLS
“Exclusive motorway lanes for your business data”
MPLS (Multiprotocol Label Switching) is a technology that assigns specific “lanes” for your data over a provider’s fibre network. When this service is available, it enables your business data to bypass public congestion, giving you low-latency connections. While great for connecting to the data centres hosting your cloud applications, MPLS is costly.
Dark fibre
“Private point-to-point motorways between key business sites”
Dark fibre is the unused fibre optic infrastructure businesses can lease outright from willing network providers. It’s like owning a private highway for your data, allowing complete control over speed, scalability, and performance. SD-WAN (the navigator) loves having it as an option to route your critical traffic. It’s a future-proof option for high-demand enterprises, albeit expensive.
ZTNA
“Security checkpoints across your WAN”
Zero Trust Network Access (ZTNA) is a cybersecurity technology that verifies every user and device attempting to connect to the WAN, ensuring only authorised traffic gets through. It’s super strict but extremely efficient border patrol for your WAN. ZTNA is more efficient and safe than VPNs, making it perfect for fully remote or hybrid work environments.
Ethernet
“The pavements and road signs underlying it all”
Ethernet is an honourable mention because it’s the technology that underlies all wired networks, including those that form WANs. It’s the protocols and software that underly cables, devices, hubs, network switches and gateways that form the internet, and therefore WANs.
Business WAN architecture
Business WAN architectures used to be rigid. It was either a centralised network, where all network resources were hosted at headquarters, or a decentralised network, where resources were distributed across multiple sites.
But with the rise of the cloud, modern WANs have evolved into hybrid architectures, blending the best of both. Some aspects, such as SD-WAN, VoIP, and cybersecurity, are centralised in the cloud, while others, like local computation and backup storage, remain distributed across on-site servers.
Here’s how hybrid architectures apply in various industries:
- A post-production studio may rely on dark fibre (superfast fibre) and SD-WAN (optimised routing) to transfer massive video files quickly between offices and cloud storage. Local servers handle rendering workloads, while cloud-based tools enable remote collaboration with global partners.
- Large banks combine MPLS (priority bandwidth) connections with SD-WAN (optimised routing) for ultra-low-latency, secure transaction processing. While customer-facing apps and data analytics are hosted in the cloud, critical systems like security compliance monitoring are distributed across regional data centres for resilience.
- Tech start-ups with fully remote teams rely on ZTNA (supersecure framework) and SD-WAN (optimised routing) to provide secure access to cloud-hosted tools like UCaaS. The minimal on-site infrastructure allows for maximum flexibility and scalability.
Whether the architecture leans centralised or decentralised, SD-WAN has become the common thread, offering flexible, efficient, and reliable performance across all types of WANs.
Designing a WAN
Designing a WAN involves several studies and requires input from experts to iron out the details. Here are the general steps required to design your WAN:
Assess your business requirements and growth plans
Identify the number of locations, data volume, and critical applications your business needs to support, ensuring the WAN can scale as your company grows.
Select appropriate WAN technologies
Evaluate all options available, balancing needs and costs. Consider technologies like MPLS, SD-WAN or leased lines to achieve your connectivity goals.
Implement robust security measures
Safeguard data with encryption, firewalls, and access controls. Consider advanced strategies like ZTNA to safeguard against evolving cybersecurity threats.
Monitor and optimise the network
Leverage performance management tools to ensure high uptime and quickly identify bottlenecks. Proactive optimisation helps your WAN meet changing business demands.
WAN optimisation
Optimising a WAN involves improving its performance, efficiency, and reliability to support business objectives. Below are the key methods for effective WAN optimisation:
Optimal connections
A WAN is only as robust as its weakest link. To ensure optimal connectivity:
- Use fibre optic technology for important site-to-site or site-to-cloud connections, offering maximum speed and stability.
- Install leased lines where possible, with failover solutions for network load balancing and reliability.
- In remote locations without full fibre business broadband coverage, complement low-spec broadband with business satellite broadband or wireless leased lines, if available.
- Ensure Local Area Network (LAN) components, like routers and network switches, are high-performance to prevent small-scale bottlenecks.
Traffic management
Efficient traffic prioritisation ensures critical applications, such as VoIP phone systems and data backups, receive sufficient bandwidth, preventing operational disruptions like poor VoIP call quality.
Employ SD-WAN and Quality of Service (QoS) technologies at the business broadband router to prioritise traffic effectively.
Network monitoring and review
Proactive monitoring and regular reviews are crucial to maintaining WAN performance:
- Utilise network monitoring tools to identify and address bottlenecks, minimising downtime.
- Conduct periodic network audits to uncover outdated equipment, underutilised bandwidth, or other inefficiencies, enabling smarter resource allocation.
Reducing business WAN costs
Effectively managing WAN costs involves balancing performance with budget constraints. Here are key strategies to reduce WAN costs:
Transitioning to SD-WAN
Switching from traditional MPLS to SD-WAN is one of the most effective ways to reduce costs. SD-WAN uses multiple, more affordable internet broadband connections to create a reliable network at a lower operational expense.
Timing broadband contracts
Evaluate your business broadband contracts as they approach renewal. This is an ideal opportunity to switch providers or upgrade services without incurring early termination fees.
Adopting a cloud-based architecture
Transitioning to a cloud-based architecture eliminates the need to manage on-site servers, licences, and infrastructure. Pay-as-you-go services offer flexibility, scalability, and reduced maintenance costs.
Network audit and optimisation
Regular network audits can identify cost-saving opportunities, such as underutilised leased lines nearing contract expiration.
Consolidating WAN connections
Streamline your network by consolidating multiple WAN connections into a single, more efficient setup. Merge connections for different sites or replace high-cost links with affordable alternatives where possible.
Negotiating with providers
Negotiate better deals with business broadband providers, leveraging your business’s loyalty or volume usage. Use a business broadband comparison service to find alternatives and uncover competitive pricing and features.
Assessing ROI
Evaluate the return on investment (ROI) of your WAN by comparing maintenance costs with their impact on productivity and growth. A high-performing WAN enhances access to cloud applications, supports remote work, and reduces bottlenecks, boosting overall efficiency.
Advanced security strategies for WANs
The growing reliance on WANs for business communication has introduced new cyberattack vectors, prompting the need for advanced security measures. Below are key strategies for fortifying WAN security:
Zero Trust Network Access (ZTNA)
Zero Trust Network Access requires verification for every user and device attempting to access the network. By assuming that no entity is inherently trustworthy, ZTNA minimises risks and ensures comprehensive protection.
Network Segmentation
Dividing the network into isolated segments limits the spread of potential breaches. This containment strategy ensures sensitive data is accessible only to authorised users, reducing the impact of attacks.
Robust Encryption
Strong encryption protocols protect data in transit, ensuring its security even if intercepted. Virtual Private Networks (VPNs) create secure, encrypted tunnels for remote access, safeguarding information over public networks.
Firewalls
Firewalls serve as a critical defence at the network perimeter, monitoring and controlling traffic to block unauthorised access and mitigate threats.
Compliance with UK Cybersecurity Regulations
Adhering to regulations like GDPR and the NIS Directive is crucial for avoiding legal and financial penalties. Cybersecurity compliance also reinforces customer trust by demonstrating a commitment to data protection.
💡Cyberattack survival: With data breaches costing UK businesses an average of £3 million, a multi-layered WAN security strategy is indispensable.
Wide Area Network (WAN) – FAQs
Our business broadband experts answer commonly asked questions about wide area networks (WANs):
What is a WAN router?
A WAN router connects multiple networks over a Wide Area Network (WAN). It handles large traffic volumes, ensuring efficient and secure communication between distant locations. Features often include network load balancing, failover support, and security protocols to enhance performance and protect against threats. WAN routers are essential for businesses to maintain reliable and high-speed connectivity.

